Worried about how to secure your company’s mobile devices? You’re not alone. In today’s digital world, smartphones and tablets are essential tools for business, but they also present a growing security risk.
Data breaches and cyberattacks are on the rise, and mobile devices are often a prime target. Sensitive company information stored on smartphones and tablets can be easily compromised if not properly protected. But don’t panic! Methods to secure your company’s mobile devices don’t have to be a complex or expensive process. In fact, with just a few essential tips, you can significantly reduce the risk of data breaches and ensure your company’s mobile fleet operates safely and securely.
Get ready to unlock peace of mind and take control of your mobile security with our simple, practical guide. Dive into the 5 essential tips below and watch your mobile security worries vanish!
5 Easy Steps to Secure your Company’s Mobile Devices
1. Establish Policies and Procedures:
- Mobile Device Security Policy: Clearly outline acceptable use of mobile devices, including password requirements, data protection protocols, and prohibited activities.
- Bring Your Own Device (BYOD) Policy: If allowing personal devices, define acceptable configurations, data segregation methods, and remote wipe capabilities.
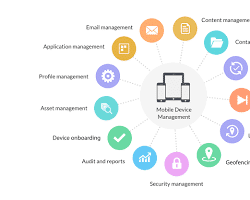
2. Implement Technology Solutions:
- Mobile Device Management (MDM): Centrally manage devices, enforce security policies, distribute software updates, and remotely wipe lost or stolen phones. The Best Android MDM Software: Features & Benefits
- Endpoint Security Software: Install antivirus and anti-malware software to protect against cyber threats. Protect your Android Device with Anti-virus app
- Data Encryption: Encrypt sensitive data at rest and in transit to prevent unauthorized access. Android Data Encryption
- Virtual Private Network (VPN): Securely connect to company networks when using public Wi-Fi. How to setup a VPN network on Android?
3. Educate and Train Employees:
- Security Awareness Training: Regularly educate employees on mobile security best practices, phishing scams, and social engineering techniques.
- Importance of Strong Passwords: Emphasize the importance of creating and using strong, unique passwords for all accounts. Secure Your Android Privacy
- Phishing and Social Engineering Awareness: Train employees to identify and avoid phishing scams and social engineering attempts.
4. Physical Security:
- Lost and Stolen Device Protocols: Establish procedures for reporting lost or stolen devices and remotely wiping them if necessary.
- Secure Device Storage: Encourage employees to store devices in secure locations when not in use.
5. Continuous Monitoring and Improvement:
- Regularly Review and Update Policies: Adapt security measures as technology and threats evolve.
- Monitor Device Activity: Use MDM or other tools to monitor device activity for suspicious behavior.
- Conduct Security Audits: Regularly assess the effectiveness of your mobile security program and identify areas for improvement.
By implementing these strategies, companies can secure your company’s mobile devices significantly and improve the security of their mobile devices and protect sensitive data from unauthorized access. Remember, mobile security is an ongoing process, and continuous vigilance is key to staying ahead of evolving threats.
Frequently Asked Questions (FAQ) to Secure Your Company’s Mobile Devices:
1. Why is securing company mobile devices important?
- Mobile devices can hold sensitive company data, making them prime targets for cyberattacks. A data breach can lead to financial losses, reputational damage, and legal repercussions.
- Protecting employee privacy is crucial, especially with BYOD (Bring Your Own Device) policies.
- Secure devices improve productivity and reduce the risk of accidental data leaks.
2. What are the main threats to mobile security?
- Malware: Malicious apps can steal data, hijack devices, or spy on user activity.
- Phishing attacks: Deceptive emails or texts can trick users into revealing sensitive information or downloading malware.
- Unsecured public Wi-Fi: Public networks can be easily eavesdropped on, exposing your data.
- Lost or stolen devices: Unprotected devices can easily be accessed if lost or stolen.
3. What are the essential strategies for mobile security?
- Implement strong password policies: Enforce long, complex passwords and regular password changes.
- Use mobile device management (MDM) software: MDM helps manage and secure all company-owned and BYOD devices remotely.
- Encrypt sensitive data: Encrypt data at rest and in transit to prevent unauthorized access.
- Enable multi-factor authentication (MFA): Add an extra layer of security by requiring additional verification codes for device access.
- Educate employees: Train employees on mobile security best practices, like avoiding suspicious apps and links, reporting phishing attempts, and using secure Wi-Fi connections.
4. What about BYOD (Bring Your Own Device)? How can we manage security with personal devices?
- Have a clear BYOD policy that outlines device requirements, acceptable use, and security protocols.
- Use containerization solutions to separate work data from personal data on BYOD devices.
- Require strong passwords and remote wipe capabilities for company data access.
- Monitor BYOD for suspicious activity and enforce policy breaches.
5. What are some additional tips for securing mobile devices?
- Install the latest security updates: Update operating systems and apps regularly to patch vulnerabilities.
- Disable unnecessary features: Turn off Bluetooth, location services, and other features not in use.
- Use a VPN for public Wi-Fi: Encrypt your connection on public Wi-Fi networks.
- Backup your data regularly: Ensure you can recover lost or stolen data.
- Stay informed about evolving security threats: Keep up with the latest mobile security trends and adapt your strategies accordingly.
Remember: Mobile security is an ongoing process. By implementing these strategies and staying vigilant, you can significantly reduce the risk of data breaches and protect your company’s valuable information.
Additional helpful information:
Find the Top 20 Business apps for Android – Top 20 Business Apps for Android